依據歐盟施行的個人資料保護法,我們致力於保護您的個人資料並提供您對個人資料的掌握。
按一下「全部接受」,代表您允許我們置放 Cookie 來提升您在本網站上的使用體驗、協助我們分析網站效能和使用狀況,以及讓我們投放相關聯的行銷內容。您可以在下方管理 Cookie 設定。 按一下「確認」即代表您同意採用目前的設定。
Latest News
中銀文摘
2021-12-14
區塊鏈專區
Supervision of Virtual Currency Platforms – Focusing on Governing Anti-Money Laundering and Countering the Financing of Terrorism
【Charlotte S. H. Wu, Partner, Zhong Yin Law Firm】
charlotte.wu@zhongyinlawyer.com.tw
charlotte.wu@zhongyinlawyer.com.tw
Ⅰ. Introduction
If virtual currencies can be freely traded, transferred, or exchanged, in other words, they can be exchanged with fiat currency through the platform exchange rate and with different kinds of virtual currencies, then the liquidity of virtual currencies may be similar to that of real currencies. However, enhanced by the anonymity of blockchain technology, the transaction risk of virtual currency is also increased. In order to address the risks posed by virtual currency transactions, Taiwan amended its money laundering law on November 7, 2018, to include virtual currency platforms and trading businesses within the scope of regulation, requiring the establishment of internal controls and audit systems for anti-money laundering and countering terrorist financing (hereinafter referred to as AML/CFT), customer identification, record keeping, reporting of currency transactions above a certain amount, and reporting of suspected AML/CFT transactions.
The Executive Yuan designated the Financial Supervisory Commission (“FSC”) as the competent authority for AML/CFT prevention in this industry[1], and the FSC issued the “Regulations Governing Anti-Money Laundering and Countering the Financing of Terrorism for Enterprises Handling Virtual Currency Platform or Transaction” on June 30, 2021, as authorized by the Money Laundering Control Act and the Counter-Terrorism Financing Act. Therefore, these platforms are subject to KYC (Know-your-clients) and CDD (Customer Due Diligence) obligations identical to those of financial institutions.
On September 30, 2021, the FSC required virtual currency platforms and trading businesses registered in Taiwan to issue an AML compliance statement[2], including a statement, a declarant Information Form, and a checklist of the AML internal controls and audit system reviewed by an accountant. The FSC also requested the statement to be completed by the end of November 2021 and the checklist to be completed by the end of June 2022 along with the names of eight platforms that must fulfill its legal compliance obligations. If the platforms continue to operate without completing the statement and fails to improve by the deadline stipulated by the FSC, fines of more than NT$500,000 and less than NT$10 million[3] will be imposed. In fact, in order to prevent virtual currency platforms from becoming a hotbed of crime, many countries are strengthening regulations to guide the industry in the implementation of AML measures.
Ⅱ. Europe
To address the risks associated with the anonymity of virtual currency and to achieve AML and CFT objectives, Directive (EU) 2018/843 of the European Parliament and of the Council[4] (hereinafter referred to as “the Directive”) brings virtual currencies, providers engaged in exchange services between virtual currencies and fiat currencies and custodian wallet providers under the scope of supervision. According to the Directive, virtual currencies means a digital representation of value that is not issued or guaranteed by a central bank or a public authority, is not necessarily attached to a legally established currency and does not possess a legal status of currency or money, but is accepted by natural or legal persons as a means of exchange and which can be transferred, stored and traded electronically. The Directive emphasizes that while virtual currencies can frequently be used as a means of payment, they could also be used for other purposes and find broader applications such as means of exchange, investment, store-of-value products or use in online casinos. Therefore, in order to improve the overall transparency of the financial environment, the objective of this Directive is to cover all the potential uses of virtual currencies.
According to the Directive, custodian wallet provider means an entity that provides services to safeguard private cryptographic keys on behalf of its customers, to hold, store and transfer virtual currencies. The Directive says if providers engage in exchange services between virtual currencies and fiat currencies but custodian wallet providers have no obligation to identify suspicious activity, illegal money laundering or terrorist organizations, then possibility exists for the engagement of criminal acts or generation of illegal benefits because of the anonymity of the platform. Therefore, it is essential to extend the scope of the Directive to include these providers and call on national authorities to establish a balanced and proportional approach to the supervision of these providers, such as ensuring that providers are licensed and registered and that risk management systems are in place.
Ⅲ. Taiwan -《Regulations Governing Anti-Money Laundering and Countering the Financing of Terrorism for Enterprises Handling Virtual Currency Platform or Transaction》
ⅰ. Definition[5] (Article 2)
1. An enterprise, registered domestically, handling virtual currency platform or transaction (hereinafter referred to as the enterprise) refers to a business that engages in the following activities on behalf of others.
(1) Exchange between virtual currencies and fiat currencies, such as New Taiwan Dollar (hereinafter referred to as NTD), foreign currencies, and currencies issued by Mainland China, Hong Kong, or Macao.
(2) Exchange between one and more forms of virtual currencies.
(3) Transfer of virtual currencies.
(4) Safekeeping or administration of virtual currencies or instruments enabling control over virtual currencies.
(5) Participation in and provision of financial services related to an issuer’s offer or sale of virtual currencies.
2. A virtual currency refers to a digital representation of value with the use of cryptography and distributed ledger technology or other similar technology that can be digitally stored, exchanged, or transferred, and can be used for payment or investment purposes. However, virtual currencies do not include digital representations of NTD, foreign currencies, currencies issued by Mainland China, Hong Kong, or Macao, securities, and other financial assets issued in accordance with laws.
ⅱ. Customer due diligence (CDD) and ongoing due diligence measures (Article 3-6, 9)
1. The enterprise shall comply with the following provisions in undertaking CDD measures on customers:
(1) The enterprise shall not accept anonymous accounts or accounts in fictitious names for establishing or maintaining business relationship.[6]
(2) The enterprise shall undertake CDD measures on customers when:
A. Establishing a business relationship with any customer;
B. Carrying out an occasional transaction[7] equal to and above NTD$30,000 or multiple occasional transactions that are obviously related with a sum total more than NTD$30,000. (Including the foreign currency equivalent thereof).
(3) There is a suspicion of money laundering or terrorist financing (hereinafter referred to as ML/TF).
(4) The enterprise has doubts about the veracity or adequacy of previously obtained customer identification data.
2. The CDD measures to be taken by the enterprise shall be as follows:
(1) Identifying the customer and verifying the customer’s identity using reliable, independent source documents, data or information.
(2) Verifying that any person purporting to act on behalf of the customer is so authorized, identifying and verifying the identity of that person using the methods specified in the preceding item.
(3) Identifying the identity of the beneficial owner of a customer[8] and taking reasonable measures to verify the identity of the beneficial owner, including using data or information from a reliable source.
(4) Understanding, and in view of the situation, obtaining relevant information on the purpose and intended nature of the business relationship when undertaking CDD measures.
(5) When the customer is a natural person, the enterprise shall obtain at least the following information on the customer to identify and verify the customer’s identity: Name; Number of official identity document; Date of birth; Nationality; Household registration or residence address.
(6) When the customer is a legal person, an organization or a trustee, the enterprise shall understand the business nature of the customer or trust (including a legal arrangement similar to a trust) and obtain at least the following information to identify the customer or the trust and verify its identity:
A. Name, legal form, and proof of existence of the customer or trust.
B. The charter or similar power documents that regulate and bind the legal person or trust, except for any of the following circumstances:
a. Customers/entities provided under Section 7(3) of Article 3 hereof (Refer to Figure I) without the situations specified in the proviso of Section 3 of Article 6 herein (Refer to Figure II).
b. The customer who is an organization is verified that it does not have a charter or similar power document
C. Names of relevant persons having a senior management position in the customer.
D. The address of the registered office of the customer, and if different, the address of its principal place of business.
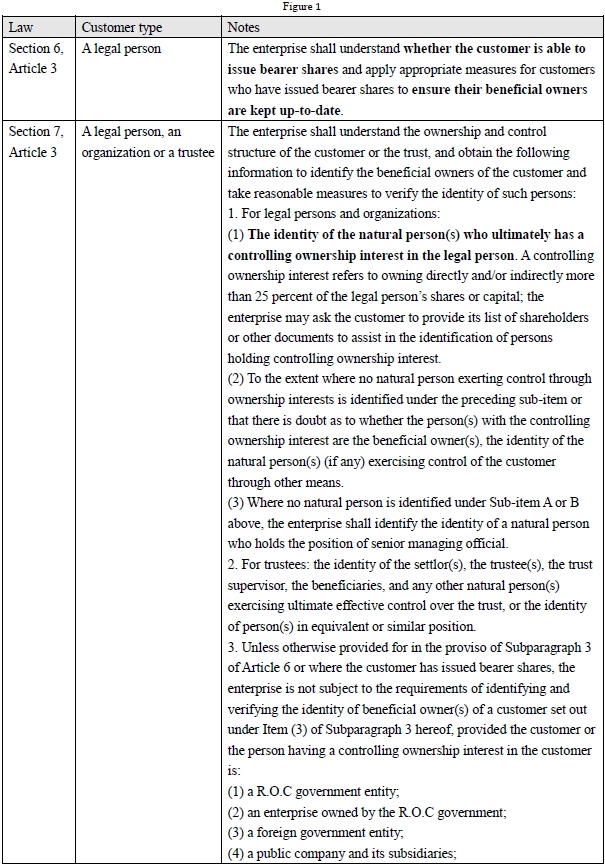
(7) The enterprise shall perform CDD measures by itself. However, if it is otherwise permitted by laws or regulations that the enterprise may rely on third parties to perform the identification and verification of the identities of customers, agents and beneficial owners or the purpose and intended nature of the business relationship, the enterprise relying on the third party shall still bear the ultimate responsibility for CDD measures and comply with the provisions[9].
(8) The enterprise shall not establish business relationship with a customer or conduct occasional transactions with a value of more than NTD$30,000 before completing the CDD measures.
(9) Where the enterprise is unable to complete the required CDD process on a customer, it shall consider filing a suspicious transaction report on money laundering or terrorist financing (STR) in relation to the customer.
(10) If the enterprise forms a suspicion of ML/TF and reasonably believes that performing the CDD process will tip-off the customer, it is permitted not to pursue that process and file an STR instead.
3. If there exists any of the following situations in the CDD process, the enterprise shall decline to establish business relationship or carry out any transaction with the customer:
(1) The customer is suspected of opening an anonymous account or using a fake name, a nominee, a shell company or legal persons/organization to establish a business relationship;
(2) The customer refuses to provide the required documents for identifying and verifying its identity;
(3) Where any person acts on behalf of a customer for establishing business relationship or conducting a transaction and it is difficult to check and verify the fact of authorization and identity-related information;
(4) The customer uses forged or altered identification documents;
(5) Documents provided by the customer are suspicious or unclear, and the customer refuses to provide other supporting documents or documents provided by the customer cannot be verified;
(6) The customer procrastinates in providing identification documents in an unusual manner;
(7) The customer is an individual, a legal person or an organization sanctioned under the Counter-Terrorism Financing Act, or a terrorist or terrorist group identified or investigated by a foreign government or an international organization, except for payments made under Section 1(1) to (3) of Article 6[10] of the Counter-Terrorism Financing Act; or
(8) Other unusual circumstances exist in the process of establishing business relationship or conducting transaction and the customer fails to provide reasonable explanations.
4. The CDD measures of the enterprise shall include ongoing customer due diligence and compliance with the provisions[11].
5. The enterprise shall determine the extent of applying CDD and ongoing due diligence measures based on a risk-based approach (RBA)[12]:
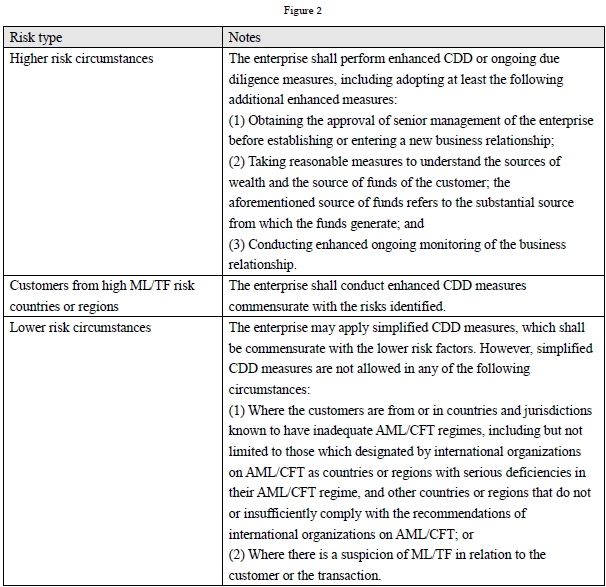
6. When conducting CDD measures, the enterprise shall put in place risk management systems to determine whether a customer and its beneficial owner is a person who is or has been entrusted with a prominent function by a domestic government, a foreign government, or an international organization.
ⅲ. The originating party and the beneficiary party of virtual currency transfers (Article 7)
1. Where the enterprise serves as the originating party of virtual currency transfers, the enterprise shall obtain required and accurate information on the customer transferring the virtual currency (hereinafter referred to as the originator) and required information on the customer receiving the virtual currency (hereinafter referred to as the beneficiary). It shall retain previously acquired information in accordance with Article 10, and submit the aforementioned information immediately and securely to the enterprise serving as the beneficiary party. Law enforcement authorities should be able to compel immediate production of such information and the enterprise shall respond accordingly. Violators are not allowed to process the virtual currency transfer.
(1) Information of the originator shall include the name of the originator, information on the wallet used for transferring the virtual currency, and one of the following information of the originator: number of official identity document, address or, date and place of birth.
(2) Information of the beneficiary shall include the name of the beneficiary and information on the wallet used for receiving the virtual currency.
2. Where the enterprise serves as the beneficiary party of virtual currency transfers, it shall comply with the following provisions:
(1) Take reasonable measures to identify virtual currency transfers that lack the required information specified in Subparagraph 2 of the preceding paragraph.
(2) Have risk-based policies and procedures for determining when to execute, reject, or suspend a virtual currency transfer that lacks the required information specified in Subparagraph 2 of the preceding paragraph and the appropriate follow-up actions.
(3) Maintain the information on the originator and beneficiary in accordance with Article 10.
3.When the enterprise transfers virtual currencies, it shall verify that the transaction counterparty (originating party or beneficiary party) is subject to and supervised for compliance with AML/CFT requirements consistent with standards set by the Financial Action Task Force on Money Laundering (FATF).
ⅳ. Establish policies and procedures for watch list filtering, based on a risk-based approach (Article 8)
The enterprise shall establish policies and procedures for watch list filtering, based on a risk-based approach, to detect, match and filter whether customers, beneficial owners or connected parties of the customers are individuals, legal persons or organizations sanctioned under the Counter-Terrorism Financing Act or terrorists or terrorist groups identified or investigated by a foreign government or an international organization.
The enterprise shall document its name and account filtering operations and maintain the records for a time period in accordance with Article 10.
ⅴ. Record keeping (Article 10)
The enterprise shall keep records on all business relations and transactions with its customers in hard copy or electronic form and in accordance with the following provisions:
1. The enterprise shall maintain all necessary records on domestic and international transactions for at least five years or a longer period as otherwise required by law.
2. The enterprise shall keep all the following information for at least five years or a longer period as otherwise required by law after the business relationship is ended, or after the date of the occasional transactions:
(1) All records obtained through CDD measures, such as copies or records of passports, identity cards, driving licenses or other similar official identification documents.
(2) Contract document files.
(3) Business correspondence, including information on the background and purpose obtained from inquiries to complex, unusual large transactions and the results of any analysis undertaken.
3. Transaction records maintained by the enterprise shall be sufficient to reconstruct individual transactions so as to provide, if necessary, evidence of criminal activity.
4. The enterprise shall ensure that transaction records and CDD information will be available swiftly to the competent authorities when such requests are made with appropriate authority.
ⅵ. Report of cash transactions (Article 11)
The enterprise shall report cash transactions with an amount equal to or above NTD$500,000 (including its equivalent in foreign currencies and currencies issued by Mainland China, Hong Kong, or Macao) to the Investigation Bureau, Ministry of Justice within five (5) business days of the transaction. The data reported to the Investigation Bureau, Ministry of Justice and relevant transaction records in the preceding paragraph shall be kept in accordance with the Article 10.
ⅶ. Ongoing monitoring of transactions (Article 12)
1. The enterprise shall comply with the following provisions for ongoing monitoring of transactions:
(1) The enterprise shall establish policies and procedures for transaction monitoring based on a risk-based approach and utilize information system to assist in the detection of suspicious ML/TF transactions. The enterprise shall review its policies and procedures for transaction monitoring on a regular basis.
(2) The policies and procedures for transaction monitoring in the preceding subparagraph shall include at least complete monitoring indicators[13], parameters setting, threshold amounts, alerts and operation procedures of monitoring, the reviewing procedures for monitored cases, and reporting standards, and shall be documented.
(3) The enterprise shall document its operation of ongoing transaction monitoring and maintain the records for a time period in accordance with Article 10.
2. The enterprise shall file suspicious ML/TF transaction reports in accordance with following provisions:
(1) For a transaction that exhibits the monitoring indicators or other irregularities set out under Subparagraph 2 of the preceding paragraph, the enterprise shall complete the review process as quickly as possible to determine whether the transaction is suspected of involving ML/TF activity, and shall retain records.
(2) Where the review has resulted in a determination that a transaction is suspected of involving ML or TF activity, regardless of the amount of the transaction, the enterprise shall promptly file an STR with the Investigation Bureau, Ministry of Justice in a format prescribed by the Bureau after the report has been approved by the responsible compliance officer at the enterprise. The report shall be filed within two (2) business days of said approval. The same shall apply to attempted transactions.
(3) For obviously significant suspicious ML/TF transactions of an urgent nature, the enterprise shall file a report as soon as possible to the Investigation Bureau, Ministry of Justice by fax or other feasible means.
(4) The enterprise shall keep the data reported to the Investigation Bureau, Ministry of Justice and relevant transaction records in accordance with Article 10.
ⅷ. Report of Section, Article 7 of the Counter-Terrorism Financing Act (Article 13)
1. After learning of the case, the enterprise shall submit the report for approval by the responsible compliance officer, and then promptly file the report with the Investigation Bureau, Ministry of Justice in the format and manner prescribed by the Bureau. The report shall be filed within two (2) business days following the date of approval.
2. In the event of an obviously significant and urgent case, the enterprise shall file a report as soon as possible to the Investigation Bureau, Ministry of Justice by fax or other feasible means.
3. The reporting records and related relevant transaction certificates mentioned in the preceding paragraph shall be maintained in accordance with Article 10.
ⅸ. Measures to identify, assess, and understand its ML/TF risks (Article 14, 16)
1. The enterprise shall take appropriate measures to identify, assess, and understand its ML/TF risks. The measures shall at least cover the customers, countries or geographic areas, products, services, transactions or delivery channels and be processed in accordance with the following provisions:
(1) A risk assessment report shall be documented every two years;
(2) The risk assessment shall consider all risk factors to determine the level of overall risk, and appropriate measures to mitigate the risks;
(3) Keeping the risk assessment up-to-date; and
(4) The risk assessment report shall be provided upon the request of the FSC.
2. The enterprise shall conduct ML/TF risk assessments before launching new products, new services or new business practices. It shall also establish appropriate risk management measures to mitigate identified risks.
ⅹ. Internal audit and internal control system for AML/CFT operations (Article 15)
1. The enterprise shall establish the system based on its ML/TF risks and business size. The system and any subsequent amendments thereto shall be approved by the board of directors. The content of the system shall include the following matters:
(1) The operation and control procedures for AML/CFT.
(2) Appoint an AML/CFT compliance officer[14] at the management level for coordinating and supervising AML/CFT operations.
(3) Establish screening procedures to ensure high standards when hiring employees and ongoing employee training programs, including examining whether the prospective employee has character integrity and the professional knowledge required to perform his/her duty, and regularly organizing or participating in on-the-job training for AML/CFT operations.
(4) Prepare and periodically update the ML/TF risk assessment report.
(5) An independent audit function to test the effectiveness of AML/CFT system[15]; and
(6) Other matters required by the AML/CFT regulations and the FSC.
2. The policies, controls, and procedures established in the system in the preceding paragraph shall be approved by the senior management, to enable the enterprise to manage and mitigate ML/TF risks that have been identified either by the country or the enterprise. The enterprise shall monitor the implementation of those controls and enhance them if necessary. It shall also take enhanced measures to manage and mitigate the risks where higher risks are identified.
ⅺ. AML compliance statement (Article 17)
1. The enterprise shall complete the AML compliance statement in accordance with the documents, information, and procedures specified by the FSC. Where the FSC orders the enterprise to provide supplementary information in the process for filing the statement and the enterprise fails to provide within the specified period, the statement shall be deemed as incomplete.
2. For the implementation of internal audit and internal control system of AML/CFT of the enterprise, the FSC may, at any time, appoint a designee or entrust an appropriate institution to conduct an inspection using risk-based approach. Where necessary, the enterprise may be required to entrust the professionals and technologists to conduct an inspection for the aforementioned implementation and submit a report to the FSC. The expenses shall be borne by the inspected entity.
3. When the FSC conducts the inspection in the preceding paragraph, the enterprise shall provide the AML-related books, documents, electronic data files, or other relevant materials. The aforementioned materials, whether stored in any other form, shall be provided, and the enterprise shall not circumvent, reject or obstruct the inspection for any reason.
Ⅳ. Conclusion
As technology advances and more and more alternative financial systems emerge, we can find that people are more focused on the transferability, convenience, and privacy of transactions, which is also the reason for the rise of virtual currency platforms. However, it is also because these modern technologies are not subject to or circumvented by the law, they often become the tools of crime. Therefore, regulating and defining said technologies to improve the existing framework is what the world is currently working on in order to more effectively detect, investigate and prevent wrongdoing, while at the same time guaranteeing technological progress and the transparency of alternative financial systems.
Currently, some countries have regulations governing the operation of overseas virtual asset platforms in their countries. For example, in Korea, if an overseas platform engages in the business of virtual assets targeting Koreans in Korea, it must submit a report to the competent authorities before it can operate; or in Australia, if the virtual asset is a financial product, the platform may be considered a financial services provider and must hold an Australian Financial Services Licensee (AFSL). Therefore, although the FSC has announced a list of eight listed virtual trading platform operators in place of the absence of a corresponding business registration program, the subsequent supervision will focus on how to proceed, how to identify, and whether the supervisory authority will be extended to other individuals or legal entities engaged in related activities, regardless of whether they are established in Taiwan or only provide services to Taiwanese customers.
Furthermore, according to Article 1, cash transactions of NT$500,000 or more should be reported. However, since cash transactions are considered transfers of fiat currency, the transfer of high-value virtual currency does not need to be reported, and is this a reporting loophole?
Except for “virtual currency with the nature of securities,” virtual currency is defined as digital virtual goods in Taiwan. Accordingly, the Tax Bureau believes that the taxation of virtual currencies can be divided into securities and non-securities. There are no actual domestic cases for the former. In terms of business tax, if the latter is considered as a payment instrument, it is not subject to business tax; however, the service fees and handling fees charged by the virtual trading platform operator will be considered as sales of labor services, and business tax should be levied on this part. In addition, in the income tax section, as long as the profit-making business has property transaction gains or losses, it should be included in the income tax scope of the profit-making business; if it is an individual, it is included in the property transaction income of the comprehensive income tax. Nevertheless, the difference between virtual currency transactions and fiat currency transactions is that the competent authorities cannot control virtual currency flow, so how the tax will be levied in the future remains to be seen in practice.

如您對上述的內容有任何意見或有興趣進一步瞭解,歡迎您聯繫我們。
Charlotte J.H. Wu 吳婕華律師
charlotte.wu@zhongyinlawyer.com.tw
TEL +886 2 2377 1858 EXT 8888
[1] Where the financial institutions and designated nonfinancial businesses or professions specified in Article 5 of the Money Laundering Control Act engage in activities specified herein, they shall execute businesses in accordance with the related AML/CFT regulations established by these central competent authorities governing target businesses and these Regulations shall not apply.
[2] FSC Orders: Taiwan Crypto Exchanges Must Complete Anti-Money Laundering Law Compliance by 11/30!, TNL Media Group, (Oct. 1, 2021), https://www.inside.com.tw/article/25022-taiwanese-government-should-strengthen-related-money-laundering-policies-related-to-cryptocurrencies.
[3] Order Ji-Guan-Yin-Fa-Zi No. 11002729181of the FSC on September 30, 2021.
[4] See Directive (EU) 2018/843 Of The European Parliament And Of The Council, https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:32018L0843#:~:text=Directive%20%28EU%29%202018%2F843%20of%20the%20European%20Parliament%20and,Directives%202009%2F138%2FEC%20and%202013%2F36%2FEU%20%28Text%20with%20EEA%20relevance%29, at 44-45, 53-54.
[5] Order Tai-Fa-Zi No. 1100167722 of the Executive Yuan on April 07, 2021.
[6] Section 1(3) Article 2, the establishment of business relationship refers to the acceptance of customer applications for registration or establishment of similar business transaction relationships.
[7] Section 1(4) Article 2, an occasional transaction refers to a transaction involving activities specified in Subparagraph 1 with an individual that has not established a business relationship with the enterprise.
[8] Section 1(5) Article 2, the beneficial owner shall mean the natural person(s) who ultimately owns or controls the customer or the natural person on whose behalf a transaction is being conducted, including those persons who exercise ultimate effective control over a legal person or arrangement.
[9] (1) The enterprise shall be able to immediately obtain the necessary CDD information. (2) The enterprise shall take adequate steps to satisfy itself that copies of identification data and other relevant documentation relating to CDD requirements will be made available from the third party upon request without delay. (3) The enterprise shall ensure that the third party it relies on is regulated, supervised or monitored, and has appropriate measures in place for compliance with CDD and record-keeping requirements. (4) The enterprise shall make sure that the jurisdiction where the third party it relies on has AML/CFT regulations in place consistent with the standards set out by the FATF.
[10] The competent authority may permit the following measures by its authority or an application:
1. Exempting the property or property interests necessary for maintaining the family life of a designated individual or the dependents. 2. Making reservations for expenses necessary for the management of the property or property interests by a designated individual, legal person or entity. 3. Permitting any payment made by a designated individual, legal person or entity to a bona fide third-party creditor, whose right is given before sanctions.
[11] 1. The enterprise shall apply CDD requirements to existing customers on the basis of materiality and risk, and conduct due diligence on such existing relationships at appropriate times, taking into account whether and when CDD measures have previously been undertaken and the adequacy of data obtained. The aforementioned appropriate times shall include at least: (1) When the customer enters new business relationships with the enterprise; (2) When it is time for periodic review of the customer scheduled on the basis of materiality and risk; and (3) When it becomes known that there is a material change to customer’s identity and background information.
2. The enterprise shall conduct ongoing due diligence on the business relationship to scrutinize transactions undertaken throughout the course of that relationship to ensure that the transactions being conducted are consistent with the institution’s knowledge of the customer, its business and risk profile, including, where necessary, the source of funds.
3. The enterprise shall periodically review the existing customer records to ensure that documents, data or information of the customer and its beneficial owner(s) collected under the CDD process are adequate and kept up-to-date, particularly for high-risk customers, whose reviews shall be conducted at least once every year.
4. The enterprise may rely on existing customer records to undertake identification and verification without the need to repeatedly identify and verify the identity of an existing customer when carrying out transactions. However, the enterprise shall conduct CDD measures again in accordance with Article 3 when it has doubts about the veracity or adequacy of the records, where there is a suspicion of ML/TF in relation to that customer, or where there is a material change in the way that the customer’s transaction is conducted or the customer’s account is operated, which is not consistent with the customer’s business profile.
[12] Section 1(5) Article 2, risk-based approach (RBA) shall mean the enterprise shall identify, assess and understand the ML/TF risks to which they are exposed and take appropriate AML/CTF measures commensurate with those risks in order to effectively mitigate them. Based on the RBA, the enterprise shall take enhanced measures for higher risk situations, and take relatively simplified measures for lower risk situations to allocate resources efficiently and use the most appropriate and effective approach to mitigate the identified ML/TF risks.
[13] See Order Ji-Guan-Yin-Fa-Zi No. 11001396511of the FSC on July 27, 2021, based on its asset size, geographic distribution, business characteristics, customer base and transaction characteristics, and with reference to internal ML and TF risk assessment or daily transaction information, the enterprise shall select or develop its own surveillance patterns in accordance with the examples listed in the Annex, in order to effectively identify alert transactions that may be ML, TF or armed expansion. Annex Reference: https://www.banking.gov.tw/ch/home.jsp?id=3&parentpath=0&
mcustomize=lawnew_view.jsp&dataserno=202107270002.
[14] The enterprise may assign appropriate personnel according to the business size, but not by the business personnel or the person who conducts independent audits in Section 1(5).
[15] The enterprise may assign appropriate personnel according to the business size, but not by the business personnel or the AML/CFT compliance officer in Section 1(2).




